The Ultimate Guide to Data Breaches

Near-daily data breaches have become a common fixture of the digital age. Week after week, major corporations and government agencies leak data by the boatload. Billions of login credentials show up on the dark web one day, then hackers take off with millions of Social Security numbers the next.
Revelations of new data breaches or privacy scandals litter the headlines of major news publications and corporations offer tersely worded statements that often deny or deflect responsibility. From the Equifax hack in 2017, in which the personal information of 143 million Americans was stolen, to the Marriott breach in 2018, where 383 million guest records and over 5 million passport numbers were stolen, data breaches have increased in frequency and severity.
This endless string of breaches fuels a black market of looted data. It’s all there for fraudsters to exploit, including names, email addresses, passwords, Social Security numbers, financial statements, medical records, credit card numbers, passport numbers, location histories, and home addresses. Troves of leaked and stolen data are being siphoned off, packaged up, and sold to the highest bidder.
Meanwhile, consumers have rapidly grown accustomed to a constant stream of emails from companies showing up in their inboxes alerting them to the fact that their accounts have been compromised or data stolen. Breach fatigue, whereby people become apathetic in the face of a never ending barrage of breaches with no end in sight, has become a common symptom.
With such a deluge of breaches, leaks, and privacy scandals, it can be hard to figure out what exactly is going on and just how worried you should be. Data, and the services it enables, are integral to your daily life. It is impossible to avoid routinely sharing data, whether that be with the government or a bank. And yet often your information is shared far beyond the party you initially share it with, invariably it makes its way through the convoluted and opaque data economy.
So what does this all mean for you? What even is a data breach? Why is your data in places it shouldn’t be? How do you protect yourself against this onslaught? The questions and uncertainty are endless.
To help, we’ve put together a comprehensive guide to understanding data breaches, identity theft, and the data economy, so that you are better equipped to understand what information is being exposed and how it is being compromised so that you can begin to take proactive steps to protect your data and identity.
- What is a data breach?
- What is a data leak?
- Major Breaches and Leaks
- What is the data economy?
- What is a data broker?
- What is identity theft?
- How does identity theft happen?
- Types of Identity Theft
- What is being done?
- How to Protect Yourself
What is a data breach?
A data breach occurs when an entity, whether it be a person, company, or government, gains unauthorized access to information. According to the European Union’s General Data Protection Regulation, a data breach is defined as “a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored, or otherwise processed.”
While it may seem that most are sophisticated hacks perpetrated by highly-skilled thieves, data breaches are often the result of hackers finding and exploiting basic security vulnerabilities in a system in order to steal information. Many of which could be simply avoided if companies followed cybersecurity best practices. Hackers then use this information to gain further unauthorized access to accounts, steal money, run ransomware attacks, or sell the data on the black market.
Stolen data runs the gamut from names and email addresses to medical and financial records, highly sensitive and private information that gives thieves the keys to your identity. Stolen passwords can be used to gain access to your online accounts. Social security numbers can be used for loan or tax fraud. Email addresses can be used for phishing. Credit card numbers can be used to make fraudulent purchases.
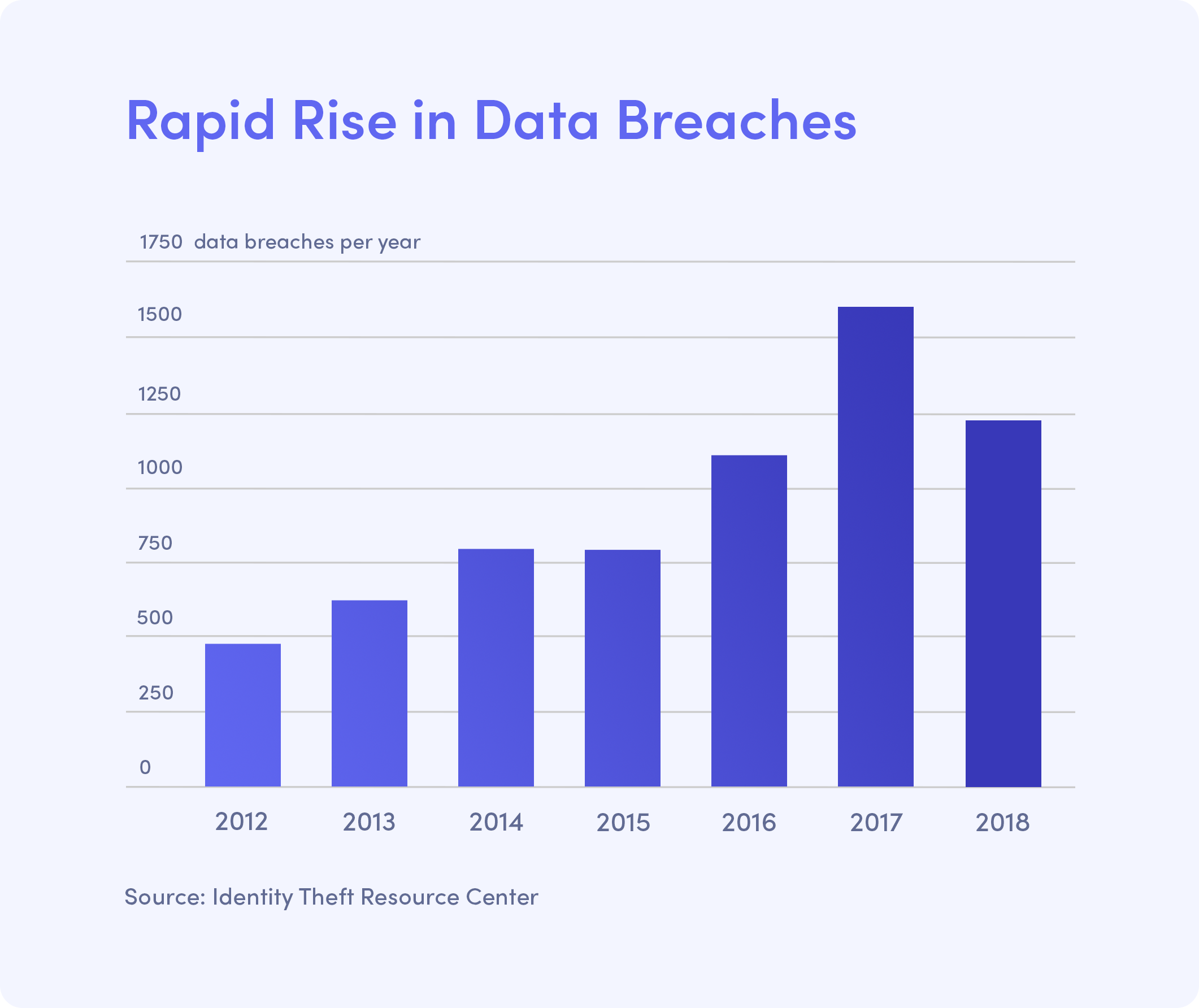
Data breaches have quickly become an epidemic. According to the Identity Theft Resource Center, there were 1,244 data breaches in 2018, up from 157 in 2005. Of those, 863 (69%) were a result of hackers gaining unauthorized access to data. Since 2005, breaches have become far more common, occurring not only more frequently but also becoming far more severe. The good news is that businesses and governments may finally be taking digital security seriously, making much needed security improvements and investing in more robust digital infrastructure.
What is a data leak?
A data leak, or exposure, is when information is accessible or visible to entities that it shouldn’t be, whether it is accessed or not. A leak differs from a breach in that it is usually the result of a company or government leaving data unprotected on a server, making it possible for anyone who stumbles upon it, especially fraudsters who are looking for these unprotected databases, to access sensitive information.
Many times it is unclear whether information has actually been accessed or stolen in an exposure. Along with breaches, leaks have become a common occurrence, some more severe than others. A database of customer names may be innocuous, but a database with millions of mortgage documents is not.
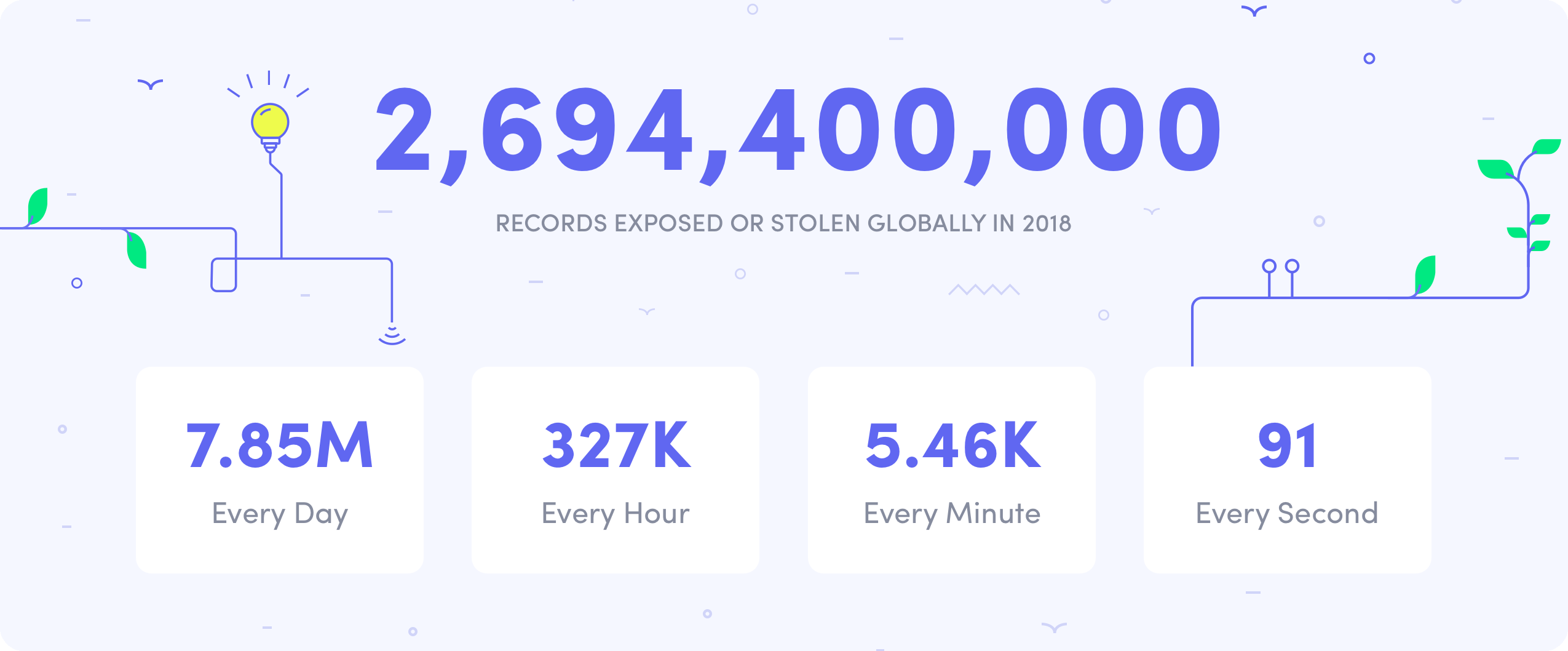
Because leaks can go unnoticed for months or even years, they pose a serious risk that nefarious actors will get access to data they shouldn’t. In 2018, there were 115 accidental data exposures in the US according to the Identity Theft Resource Center. All told, 2.69 billion records were exposed or stolen around the globe in 2018. 7.85 million every day. 327 thousand every hour. 5.46 thousand every minute. 91 every second.
Major Breaches and Leaks
While there have been thousands of breaches over the past few years, there are a few that stand out for their particularly egregious security shortfalls and the seriousness of the risk that they have exposed millions of people to. Here are the most alarming breaches of the past few years.
The Equifax Hack, September 2017
- Number of Identities Exposed: 147 million
- Information exposed: Names, Social Security numbers, birth dates, addresses, and driver’s license numbers
- Learn More: Equifax One Year Later - 4 Things You Need to Know
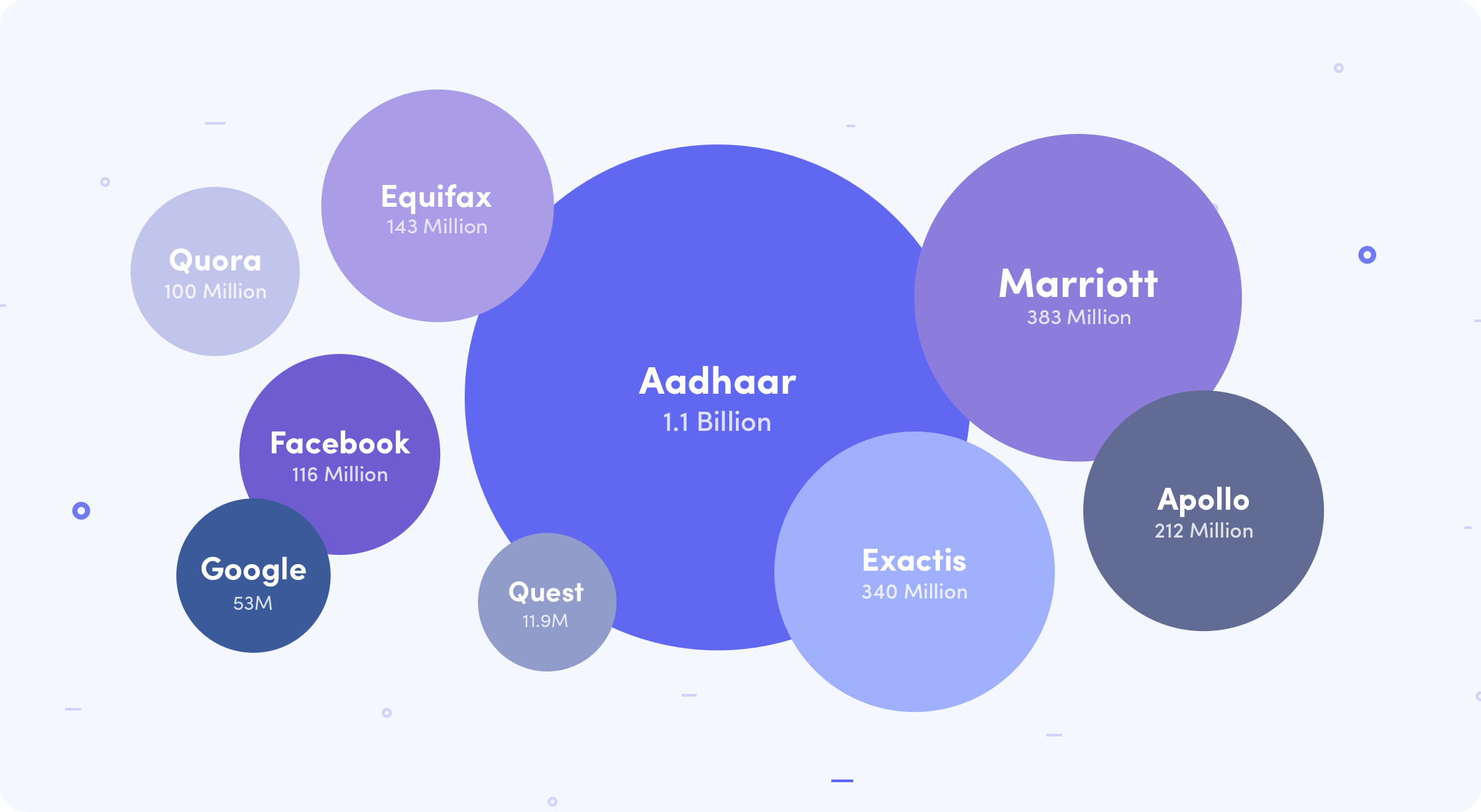
The Equifax data breach was one of the most severe and alarming data breaches in US history. On September 7, 2017, Equifax announced that 143 million American’s personal and financial information, including names, social security numbers, addresses, birthdates, and credit card numbers, had been illegally accessed and stolen by hackers. The data breach exposed the highly sensitive private information of nearly half of the American population and put 147.7 million Americans at significantly increased risk of identity theft.
What made the Equifax hack so severe was the number of Social Security numbers stolen in the breach. In the US, your Social Security number is the key to your identity. When exposed, it opens you up to all kinds of potential forms of fraud that can negatively impact your financial life for years to come. The second Equifax was breached, the identities and well-being of more than a hundred million Americans was immediately put at risk.
Everything a fraudster needs to authenticate themselves for most loans: SSNs, birth dates, driver’s license numbers, and home addresses were stolen in the Equifax hack. Accurate, secure, and credible credit information is vital to consumers looking to access loans, get a job, buy a home, or rent an apartment. As this personal information is leaked and compromised, the credibility of both the data and the agencies responsible for safeguarding it is put into doubt.
The Aadhaar Breach, January 2018
- Number of Identities Exposed: 1.1 billion
- Information Exposed: Names, unique ID numbers, and bank accounts of Indian residents
- Learn More: Report on Data Security - Aadhaar Meltdown in India
The Aadhaar breach, which was first reported in January 2018 following an extensive investigation by the Tribune, gave anyone who paid 500 rupees (approximately $7) to fraudsters on WhatsApp access to an official portal that allowed them to enter an Aadhaar number and instantly get access to the user’s name, address, postal code, photo, phone number, and email address. For an additional 300 rupees the fraudsters would print a fraudulent Aadhaar card. The WhatsApp scheme has been ongoing for months.
Aadhaar is India’s national biometric identity system. Since its inception in 2009 over 1.1 billion unique identification numbers have been assigned under the system. It is one of if not the largest databases of biometric and demographic identity data in the world. Aadhaar works through a network of local government agencies and private participants who onboard citizens onto the system under the purview of the Unique Identification Authority of India (UIDAI) , scanning fingerprints, taking images of irises, and running facial-recognition scans of residents, who are then issued 12-digit unique identification numbers.
The UIDAI has stood steadfast by its claim that no biometric data has been compromised since Aadhaar’s inception, and that without that data, which is used for authentication, hackers are unable to hijack identities. Even so, leaked data associated with Aadhaar has put hundreds of millions of Indian citizens and residents at increased risk of identity fraud and compromised bank account information has already lead to significant financial damages.
The Cambridge Analytica Scandal, March 2018
- Number of Records Leaked: 86 million
- Information Leaked: Names, birthdays, public profiles, places of residence, page likes, messages, and more
- Learn More: Report on Data Security - Failure at Facebook
In March 2018, the Cambridge Analytica scandal broke when the New York Times reported that the private data of over 86 million Facebook users had been leaked to the political consulting firm Cambridge Analytica. The data was harvested under false pretenses by a quiz app, thisisyourdigitallife, developed by Aleksandr Kogan to aide academic research.
Kogan began harvesting the data in 2014, spending roughly $800,000 to collect data on the 86 million users. Of those, only 270,000 had provided consent, although those who did were unaware of the more nefarious purposes of the app. Not only did Kogan gain access to the data of users of the app, but he also gained access to the data of all of their Facebook friends as well, completely unbeknownst to them.
What made the revelation such a bombshell was the manner in which the data was used, far removed from what users originally consented to. Kogan sold the harvested data to Cambridge Analytica, a political consulting firm that then used the data to identify personality traits and build psychographic profiles of American voters in an attempt to influence the 2016 US presidential election.
It was quickly revealed that Facebook had known about the data harvesting for over two years and had tried to quietly get the firm to delete the data, without ever warning users that their personal information had been siphoned off. What Cambridge Analytica showcases is the extent to which data is harvested and mined on a daily basis by tens of thousands of companies around the world and just how vulnerable these companies are to data leaks.
The Marriott Data Breach, November 2018
- Number of Records Stolen: 383 million
- Information Stolen: Names, addresses, dates of birth, passport numbers, email addresses, phone numbers, and encrypted credit card numbers
- Learn More: Passport Data Stolen in Marriott Data Breach
Marriott first disclosed a massive breach of its Starwood reservation system in November of 2018, announcing that the breach exposed the personal and financial information of 500 million guests. At the time, Marriott said that stolen reservation records included names, addresses, dates of birth, passport numbers, email addresses, phone numbers, and encrypted credit card numbers.
Marriott first learned of the breach in September of last year. Initially, Marriott found a spyware tool known as a remote access trojan and a penetration tool called Mimikatz on the Starwood systems but found no evidence that customer data had been accessed. It wasn’t until November that Marriott discovered that hackers had access to the system since July 2014.
According to recent testimony by Marriott CEO Arne Sorenson, in the end the company determined that 383 million guest records were stolen, which included 18.5 million encrypted passport numbers, 9.1 million encrypted payment card numbers, 5.25 million unencrypted passport numbers, and 385,000 valid card numbers.
As with many other high profile breaches, it took Marriott months before they decided to alert customers or regulators to the breach. The scope and scale of the Marriott breach makes it one of the most egregious data security incidents in years.
The First American Data Leak, May 2019
- Number of Records Exposed: 885 million
- Information Exposed: Social Security numbers, bank statements, bank account numbers, tax records, wire transactions, and drivers’ licenses
- Learn More: This Week in Data Breaches - First American Data Leak
In May of 2019, real estate and title insurance giant First American leaked hundreds of millions of mortgage related documents online. The exposed documents, which go as far back as 2003, included bank statements, tax records, bank account numbers, Social Security numbers, wire transactions, drivers’ licenses, and more. In total, 885 million financial documents were exposed on First American’s website, available for anyone with a web browser to access.
The First American data leak provided a massive treasure trove of data to fraudsters and put millions of home buyers and sellers at heightened risk for a wide-range of identity fraud. Security experts predict that the leak will be a boon for phishers and scammers who could use the information for email compromise scams, where fraudsters impersonate real estate agents or escrow firms in an attempt to trick home buyers into sending wire transfers to them.
Since the leaked documents included nearly every bit of private, sensitive information that one could provide, it would also make it easy for identity thieves to potentially open up bank accounts under the victims’ names, take out unauthorized lines of credit, or commit tax fraud by filing fraudulent tax returns. Leaks of this magnitude, with such a breadth of financial information, expose all the keys to your identity and financial life in an instant. While it is unclear if anyone improperly accessed the data while it was left unprotected, it is clear that companies who handle sensitive financial data are still not taking the necessary steps to protect consumers.
The Quest Diagnostics Data Breach, June 2019
- Number of Identities Exposed: 11.9 million
- Information Exposed: Patient names, dates of birth, addresses, Social Security numbers, phone numbers, dates of service, care providers, and credit card and bank account information
- Learn More: This Week in Data Breaches - Quest Diagnostics Data Breach
Quest Diagnostics, a laboratory testing provider, disclosed in June that a third-party vendor suffered a breach in which the personal information of 11.9 million Quest patients was stolen. The stolen data included patient names, dates of birth, addresses, Social Security numbers, phone numbers, dates of service, care providers, and credit card and bank account information.
Quest’s systems were not directly affected by the security incident, rather it was a third-party billing provider, American Medical Collection Agency (AMCA), that was compromised. An “unauthorized user” had access to AMCA’s systems for nine months, from August 2018 through March 2019.
The Quest Diagnostics incident is reminiscent of the breach at Anthem in 2014 in which the records of 79 million customers were stolen, making it the largest hack of medical data in history. Financial data handled by insurance and billing companies is extremely lucrative for hackers and continues to be a prime target. There were more than 363 data breaches in the medical sector alone last year, according to the Identity Theft Resource Center.
With so many massive data breaches and leaks in recent years, it is reasonable to ask who or what is to blame? How is it possible that billions of records can be stolen year after year? If you’re looking for a culprit, look no further than the data economy of the digital age.
What is the data economy?
As you shop online, buy a home, get married, post selfies, message friends, register to vote, like a Facebook page, and generally go about your digitally connected life, massive pools of data about you are collected, mined, and sold for profit. These ever-inquisitive digital eyes surveil your every action, every communication, building an exhaustive digital profile of your life, often without your consent and knowledge.
The data economy is a global ecosystem in which information is accumulated, mined, and monetized, turning data into an asset which is then sold and exchanged in the marketplace. This global marketplace is comprised of tens of thousands of buyers and sellers that traffic in consumer data. In the data economy, your behavior is tracked and cataloged, then predicted and modified, as data producers and platform owners tease out and manipulate your habits and preferences.
Worst of all, data security is often lacking. Social security numbers are still sometimes transmitted in plain text, making it exceedingly easy for hackers and intruders to capture them in route. Companies rarely adhere to best data security practices or fail to offer encryption whatsoever. These exploitative practices are hidden in arcane privacy policies and user agreements that no one ever reads, nor has the time or the technical know-how to understand.
Lenders can use it to offer higher-interest loans to targeted groups. Patients may face higher insurance premiums based on what are perceived as risk factors to insurance companies. Internet service providers, such as AT&T, Comcast, and Verizon, sell your browsing data on to other companies. Social media companies like Facebook collect and analyze your posts, tweets, likes, comments, and photos. Search engines track and sell your search history. Political firms use it to build psychographic profiles.
Marketers use it to predict whether you are depressed, unfaithful, or looking to quit your job. Data can be used for far more insidious purposes that you would think, even making it easier for companies to prey on the vulnerable with predatory loans or high-interest credit cards. By its very nature, an opaque data economy that exists in the shadows can lead to all kinds of exploitation or exclusion.
The list goes on and on. The market for consumer data reaches into the tens of billions, and that’s not taking into account the revenue of Big Tech, which harnesses your data to provide targeted ads and sells it on to other companies who do the same. And as data has become commoditized, as it has been accumulated to an unprecedented degree, it has led to an ever-greater amount of information being stored in centralized honeypots all over the world. And within this economy exists a seedy, yet completely legal underbelly of data brokers.
What is a data broker?
Data brokers are third-party entities that collect personal data from primary sources, aggregate it, and then sell it on to whoever is willing to pay.
Data brokers get your information by scraping public records, such as the DMV, court records, voter registration data, marriage licenses, and property records. They also buy data from other companies, such as purchase histories from retailers, and often trade data amongst themselves. These data brokers exist in the shadows, with most people going about their lives entirely unaware of their existence, even as the data itself impacts and molds the opportunities afforded to them.
They operate without consent and without regulation, as opaque as it gets. While credit reporting agencies are regulated by the Fair Credit Reporting Act, data brokers don’t fall under this framework and aren’t required to share their data with consumers or make corrections. If information is inaccurate, there is no recourse to getting it fixed. Opting-out of data brokers is time-consuming, confusing, and difficult. Requests are often simply ignored.
Data brokers have proliferated in recent years. Large firms like Acxiom, Epsilon, and Oracle Data Cloud reap massive financial rewards from the data they collect and sell. Acxiom stores files on over 700 million consumers around the world, with each file containing over 1,500 unique data points. In total, Acxiom collects more than 50 trillion pieces of data each year. And there are tens of thousands of companies just like it, harvesting data on you every single day.
These cavernous stores of personal information allow these companies to reap billions in profit off the backs of the consumers who produce it as they analyze the data for insights and patterns, and then sell it on to banks, credit card issuers, insurance companies and whoever else is willing to pay. It’s a $200 billion industry. And the three major credit bureaus in the US are brokers in their own right, with Equifax bringing in $3.4 billion annually, mostly from selling data, personal information which consumers never consented to giving Equifax in the first place.
According to the Consumer Financial Protection Bureau (CFPB), Equifax collects information from 10,000 data furnishers, and has over 200 million consumer files that contain information on 1.3 trillion trade lines. Overall, the three major credit bureaus rake in over $10 billion in revenue from selling your most private and confidential information each year.
Data brokers compound the problem of data breaches and leaks, making it increasingly hard to control who has access to your data and figure how exactly it is being used. As personal data is liberally shared and sold by an industry that lacks accountability and transparency, it puts millions of consumers in harm's way, whether it be from identity thieves or bad actors looking to target specific individuals.
What is identity theft?
Identity theft is the unauthorized access to and use of another’s personally identifiable information, such as their name, Social Security number, or credit card number, for fraudulent purposes or financial gain. Identity theft and identity fraud are often used interchangeably. If someone has used your personal information to file a tax return, take out a loan, or make fraudulent credit card purchases, it is identity theft. There are all kinds of ways fraudsters can get ahold of your information to commit identity theft, whether it be from a data breach, a lost wallet, or a phishing scam.
Stolen information used for identity fraud may include a person’s name, date of birth, Social Security number or other government-issued identification number, bank account or credit card numbers, PIN numbers, signature, fingerprints, online usernames and passwords, or any other type of personal information that is used to gain unauthorized access to resources of the victim. Often victims do not know how or where their information was obtained, making it difficult to figure out to what degree their identity has been compromised.

Identity theft is one of the fastest growing crimes in America. Since 2012, 1 in 3 Americans have been victims of identity theft, causing $120 billion in financial losses for consumers. In 2018 alone, there were over 14.4 million victims of identity fraud, leading to $14.7 billion in financial losses, according to Javelin Research & Strategy.
Victims of identity theft must deal with the destructive nature of data breaches firsthand, whether their credit has been demolished by card fraud, bank accounts emptied, or lives upturned by all kinds of other fraudulent activity. Identity theft, driven by new account fraud and account takeover, affected 5.66 percent of consumers in 2017, as fraudsters continue to use more sophisticated tools and schemes to defraud consumers.
How does identity theft happen?
Along with data breaches and leaks and the continued use of unencrypted data sharing methods that make hackers jobs even easier, there is a wide array of tools, scams, and methods that thieves use to steal personal information. Some of these tools are so easy to use that even the least sophisticated of hackers or bad actors are able to get access to loads of personal data.
Identity thieves can also steal your personal information the old fashioned way in the analog world, whether it be through ATM skimming, where fraudsters illegally place a card reader on an ATM to siphon off credit card details, dumpster-diving for thrown out credit card offers or bank account statements, or stealing mail directly from mailboxes. Imposter scams are also common and often occur over the phone, with a scammer pretending to be calling from a trustworthy source such as a bank or the IRS in an effort to steal personal information or money.
Phishing, where either identity thieves or hackers attempt to trick someone into clicking on a link in an email or text message, is one of the most insidious ways identity theft occurs. The malicious link or attachment in a phishing attack then sends the target either to a fraudulent website that is setup to look legit in attempt to get the person to enter personal information or installs malware in the background that allows the perpetrator to siphon off personal information from the device. More sophisticated phishing attacks use information stolen in a breach or leak to personalize the attack to the target, using private information that only a trustworthy friend or company would know in order to lure the victim into clicking on the malicious communication.
Unprotected Wi-Fi networks at coffee shops, airports, or other venues that offer free public Wi-Fi can also be used for identity theft. Much of the web traffic on these networks is transmitted unencrypted, making it easy for thieves to intercept browsing activity, emails, login credentials, and credit card information. In some cases, hackers have taken this a step further by setting up fake wireless access points at busy public locations, so-called “Wi-Fi honeypots”, with the sole intention of intercepting data and installing malware on connected devices.
Once identity thieves have your personal information, depending on what information or accounts they have access to, they could make fraudulent credit card purchases, take out a personal or auto loan, drain your bank account, open new utility accounts, seek medical treatment under your health insurance plan, or file a tax return in your name and get your refund.
Complex identity fraud schemes make it hard for both consumers and businesses to stay ahead of fraudsters. Prevention is also reliant on detection, and it can sometimes take days or weeks before individuals realize they have become victims.
Because so many types of identity fraud pose an acute risk to financial well-being, the potential harmful effects can be severe. Victims can suffer from the consequences for months or even years into the future. Knowing how your information could be stolen and what types of fraud to be on the lookout for are the first steps in protecting yourself against identity theft.
Types of Identity Theft and Fraud
There are so many identity theft schemes, scams, and tools that it can be hard to wrap your head around all the different types of fraud that can occur, from phishing scams that lead to account takeover to data leaks that result in tax fraud. So we’ve compiled a list of the most common types of identity theft, how often they occur, and what that means for you.
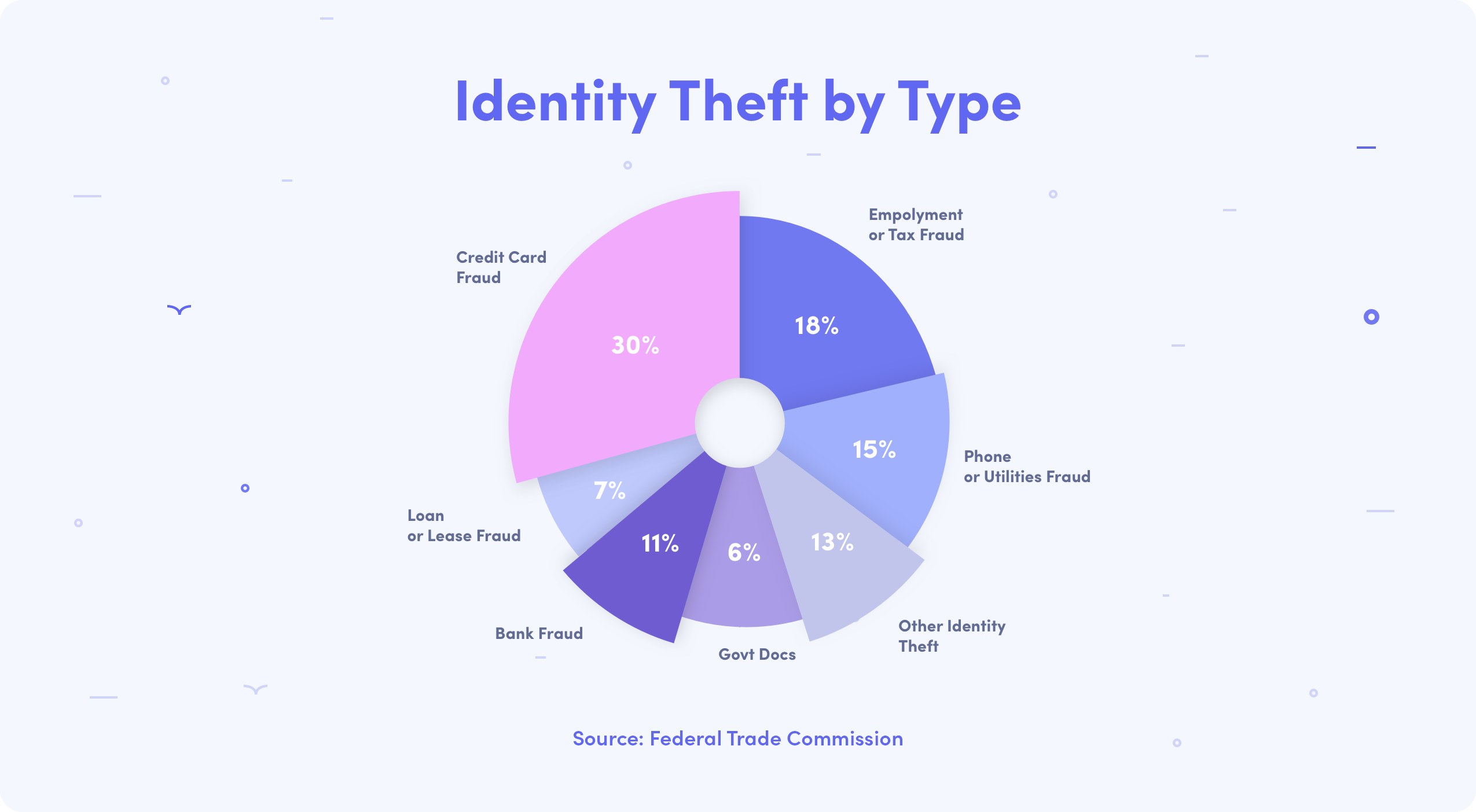
Credit card fraud was the most common type of identity theft in 2017, accounting for 30% of identity theft reports to the Federal Trade Commission. Existing account card fraud was up by 20% from 2016. Credit card fraud was followed closely by tax fraud at 18%, phone or utilities fraud at 13%, bank fraud at 11%, loan or lease fraud at 7%, government documents or benefits fraud at 6%, and other types of identity theft accounting for the remaining 15%. Here are some quick and handy definitions for the different types of identity theft and fraud to be on the lookout for.
Synthetic Identity Theft: Synthetic identity theft, a relatively new type of identity theft, occurs when a fraudster creates a new fabricated identity using bits and pieces of real identities, usually using Social Security numbers, names, addresses, and birth dates stolen from multiple people. Synthetic identity theft exploits common issues that the three major credit bureaus face, such as misspellings, name changes, and relocations, and showcases just how sophisticated and complex identity theft has become. Synthetic identity theft primarily harms lenders and banks, but if a thief uses someone’s real Social Security Number to commit synthetic ID fraud it can cause real problems for the unwitting victim.
Medical Identity Theft: Medical identity theft is the use of someone else’s health insurance to get medical care in their name. Medical ID theft can cause all sorts of problems, from inaccurate medical histories that can lead to a patient getting the wrong care or medication to victims being left in the lurch with sky hill medical bills for care they did not receive. If the victim does not catch the fraud quickly, it can lead to debt collections that serve a major blow to their credit score, making it difficult to obtain a mortgage, auto loan, or rent an apartment until they are able to get it resolved.
Child Identity Theft: Child identity theft is the use of a child’s Social Security number to commit fraud. Children are acutely susceptible to identity theft because often parents don’t think to monitor their credit reports for new activity, making it easy for identity thieves to go undetected for years as victim’s don’t usually realize fraud has occurred until they are old enough to apply for a credit card or rent an apartment. Over 1 million children were victims of identity theft in 2017, causing $2.6 in financial losses according to Javelin Strategy & Research. And 66% of children who suffer from identity theft are 0 to 7 years old.
Tax Identity Theft: Thieves often use imposter scams and phishing attacks to impersonate the IRS in an attempt to steal personal information and commit tax fraud. Tax fraud occurs when a fraudster uses someone else’s personal information to fraudulently file a tax return and claim their refund. Tax fraud is often not detected until the taxpayer receives notice from the IRS that a return has been filed. According to the Federal Trade Commission, there were 67,374 reports of tax fraud in 2018.
New Account Fraud: When fraudsters open new financial accounts or take out loans using a victim’s personal information it is new account fraud. Mortgages, student loans, car loans, and credit cards are common targets for new account fraud. Fraudsters can also open new phone or utility accounts using stolen information as well. NAF has been on the rise in recent years, with losses increasing from $3 billion in 2017 to $3.4 billion in 2018.
Credit Card Fraud: Credit card fraud is a type of Existing Account Fraud, along with bank account and insurance fraud, that includes both unauthorized transactions using counterfeit cards, as well as card not present fraud which usually occurs when a credit card number is fraudulently used online. The recent and, by international standards, late arrival of the EMV card standard in the United States has helped alleviate counterfeit card fraud to a degree. EMV cards use an integrated chip for authentication and make it much harder to produce counterfeit cards. Even with this progress, credit card fraud still occurs at a relatively high rate and is the most common type of fraud.
Account Takeover: When hackers or fraudsters gain unauthorized access to a personal or financial account and take over control it is considered an account takeover. Along with new account fraud, account takeover is the fastest rising type of identity fraud, with mobile account takeovers increasing from 380,000 in 2017 to 679,000 in 2018. Credential stuffing has helped fuel this increase, making it possible for hackers to rapidly try millions of stolen login credentials and easily gain access to thousands of accounts at a time.
What is being done?
In the US, federal data privacy legislation looks to be gaining momentum in Congress. Large corporations that continue to fail to take responsibility for their lax data security practices and exploitative privacy practices will continue to lose trust from consumers, while companies that proactively work to protect user data will make rapid inroads. Those companies who enable privacy by design, who protect the data that is entrusted to them, will begin to win out over those whose business models depend on the exploitation of user data.
2018 brought with it a global privacy trend to hold companies accountable for how they collect, store, and use data, starting with the European Union’s General Data Protection Regulation on through to California’s Consumer Privacy Act. Regulators, if not companies, have taken notice and are beginning to take the data crisis seriously. Less data breaches are possible but the culture must change.
Americans are still left with no overarching national privacy protections as breaches intensify and millions become newly minted victims of identity theft every year. A unified regulatory framework would help protect consumers and make for easier compliance for companies, who currently face state-by-state data breach laws, along with HIPAA, Gramm-Leach-Bailey, COPPA, and FERPA, depending on who their customers are.
Meanwhile, basic security oversights can be easily remedied. More resources need to be allocated to security, and the reporting of vulnerabilities needs to be properly incentivized. However, so long as data continues to be centralized it will be vulnerable to a single point of failure. Biometric data, cloud storage, and digital identity systems will all come under increased attack. Financial institutions face acute risk given the sensitive information they hold.
Broken identity systems, like Aadhaar in India and the Social Security number system in the US, require rethinking from the ground up. Companies and governments must begin looking toward new data storage and sharing models that entail local storage, public-key encryption, limited access, data minimization, and consumer ownership, and which are built with privacy by design.
How to Protect Yourself
So how can you safeguard your data and protect your identity in a world of never ending breaches and leaks? While it is more important than ever to take proactive steps toward safeguarding your data and protecting your identity online, figuring out how to best protect your identity, and trying to navigate your way through all of the advice that is out there, can be a confusing, frustrating, and time consuming process. Luckily, we are here to help.

We've put together an easy to understand guide on how to protect your identity and minimize your risk of identity fraud. Check out the steps below to get started:
- Freeze Your Credit: One of the most effective ways of reducing the risk of identity fraud is to freeze your credit. Freezing your credit will help prevent fraudsters from opening up new financial accounts or lines of credit in your name. To get started click here.
- Setup a Password Manager: Password managers make it easy to generate strong, unique passwords for every account you have, track and manage all of your passwords in one place, and prevent one account compromise from cascading into an all out security meltdown. For more information click here.
- Monitor Your Credit & Identity: By monitoring your credit reports for suspicious changes or new accounts, you can quickly identify fraudulent activity when it occurs and take steps to mitigate the damage. To get started click here.
- Enable Two-Factor Authentication: 2FA is an extra layer of security used to make sure that the person who is trying to get access to an account is who they say they are. Two-factor authentication makes it much harder for hackers and identity thieves to get unauthorized access to your online accounts. For more information click here.
- Minimize Data Sharing: Try to minimize the amount of data you share as much as possible and provide the least amount of information that is necessary. Don’t share personal information just because someone asks for it, ask why the information is needed and how it will be protected. Avoid sending plain text data or passwords by email or text, and transmit information securely whenever possible.
- Stay Vigilant: As always, the best way to protect your data and identity is to stay vigilant and to always be on the lookout for suspicious activity. Never click on links you receive by email or text that you don’t recognize. Watch out for imposter scams and phishing attacks. Never give out personal information to anyone or any company you don’t know or haven’t reach out to directly.
For more tips check out our full guide on how to protect your identity.
Bloom: Take Back Control of Your Data
With Bloom, your data will never be collected, shared, or sold without your explicit permission. Bloom allows you to verify your identity and apply for credit with third-parties without exposing your underlying data, greatly reducing your risk of identity theft. By being able to prove your identity, income, employment, creditworthiness, and more with Bloom, you won’t have to unsecurely submit forms and documentation every single time you apply for a credit card, personal loan, or apartment.
At Bloom, we are giving you the tools to take back control of your data. No more centralized data storage. No more selling off your data to the highest bidder. No more risking identity theft. Bloom enables you to own, control, and protect your data using the latest advancements in blockchain technology.
It’s time to take back control of your data and unlock the power of a secure, reusable identity today. Download the Bloom mobile app to build a cryptographically secure identity and get free data breach alerts with Radar!

