6 Ways a Site Can Attack your MetaMask
Note: You now test out these vulnerabilities in a safe environment on www.ETHwalletSecurity.com
Security is a core pillar of Bloom. It’s what led us to create a secure, decentralized identity in the BloomID. We believe that all users should have a safe and good experience when interacting with products. It’s the context for how we think about our platform — from our smart contracts, to our dApp, to how users interact with our protocol.
This also means thinking broadly about the user experience of our community as a whole.
MetaMask is an innovative Chrome extension that allows you to interact with the Ethereum blockchain, including the Bloom dApp, through your web browser. It manages your wallets and allows you to seamlessly issue transactions and vote in our Bloom platform from the web. We strongly believe that the entire crypto space has greatly benefited from the services that MetaMask provides — it’s a fantastic tool.
Due to the fast moving nature of the space, we also know that security is an ongoing evolution, so we would like to proactively point out a few possible attacks that users should be aware of.
Two weeks ago, we wrote a blog post about a theoretical attack vector against MetaMask. Today, Bloom advisor and security researcher Brandon Arvanaghi created a proof-of-concept site EthWalletSecurity, an independent project that interactively demonstrates this attack vector, along with an extended look at MetaMask’s attack surface, for all MetaMask users.
We encourage any MetaMask user to explore this site and interact with the attack vectors presented. We care deeply about the Bloom community’s security, which is why we go to great lengths to discover potential attack vectors and educate users on the potential threats they pose.
These attacks can happen to both unlocked and locked MetaMask accounts. I will address both in this article. Let’s start by taking a look at unlocked accounts.
Part 1: An Unlocked MetaMask
Your unlocked MetaMask exposes the currently selected address in MetaMask to every tab you have open. If you ever switch between accounts in MetaMask while it’s unlocked, every tab you have open will also know about that other account.
Since the blockchain is public, knowing an account’s address is enough to tell you every incoming and outgoing transaction in its history. If you visit EthWalletSecurity with an unlocked MetaMask, it shows how any site owner can use Etherscan to see your most recent incoming and outgoing transaction.
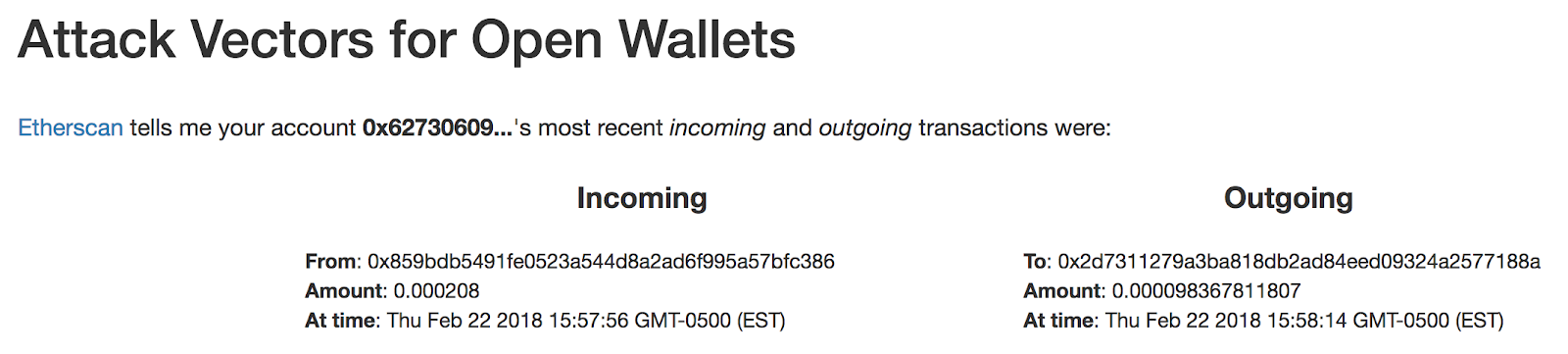
From knowing your most recent transactions, an attacker can leverage highly targeted campaigns against your MetaMask wallet.
Here’s how it could happen:
Approach #1: Your Last Outgoing Transaction Failed
The first example on EthWalletSecurity demonstrates how the site can produce a fake MetaMask notification stating that your most recent outgoing transaction failed. The fake notification would have all the real details about your last outgoing transaction, including its value, the destination address, and the date.
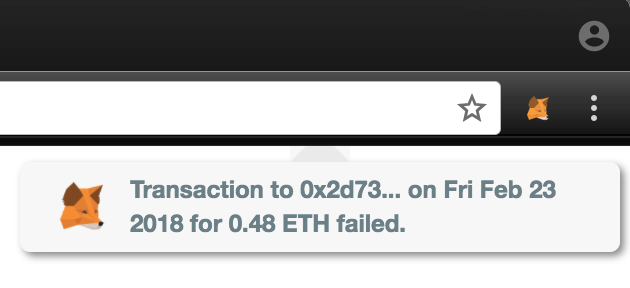
Upon hovering over this fake notification, EthWalletSecurity shows how the site can present you a MetaMask transaction for the same amount, but subtly to a different address. Because there is no standard for how Chrome extensions present notifications, a MetaMask user would have no way of knowing that this kind of pop-up, which created a transaction upon hovering over it, is fake.
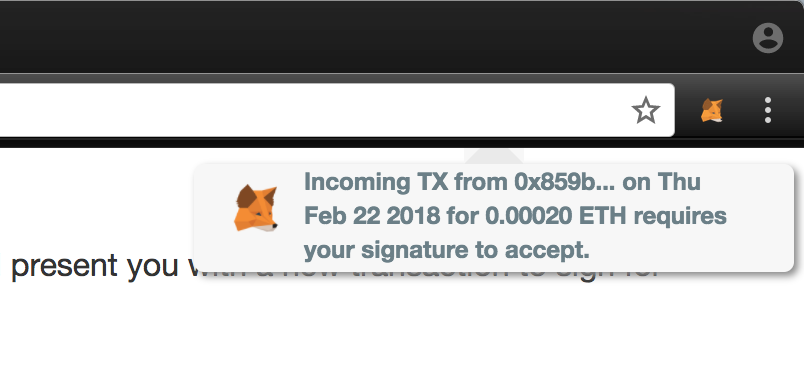
Approach #2: Sign For Your Last Incoming Transaction
Similarly, the site could take your most recent incoming transaction, with the real details about the sender address, ETH amount, and date, and claim that MetaMask requires a signature to accept it. This is not unlike signing for a package arriving at your door.
While experienced blockchain users will know that incoming transactions do not require any action on the recipient’s side, it may be easy to overlook this detail when a MetaMask lookalike presents accurate details about your most recent transaction.
Approach #3: Cloning MetaMask’s CSS
A malicious site could take the CSS of the MetaMask pop-out and make an identical, interactive version that shows accurate details about your most recent transactions, like so:
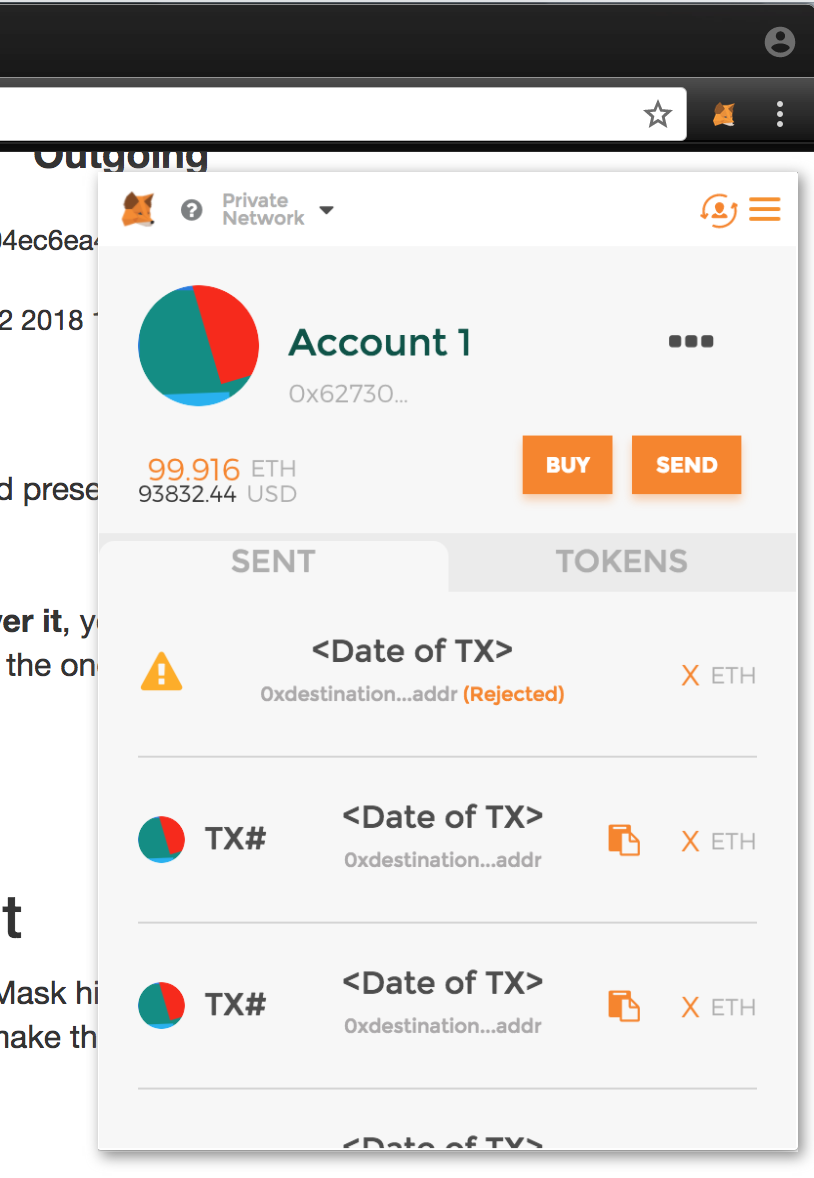
The phony pop-out would populate itself with your transaction history from Etherscan, with the exception of your most recent transaction, which the pop-out would maliciously claimed failed. The pop-out could then encourage you to re-issue the same transaction, swapping out only the destination address in the new transaction. This is identical to how MetaMask would show a real transaction failing when you click the extension.
Part 2: A Locked MetaMask
Browsing the web with a locked MetaMask does not expose any of your MetaMask addresses to any sites. However, it does tell every site you visit that you are a MetaMask user.
Approach #4: Coercing the User to Unlock Their Real MetaMask
As mentioned earlier, visiting a site with an unlocked MetaMask means that site (along with every tab you have open) will know your wallet address, its balance, its tokens, and all of your transaction history. For an advertiser, this might be their entire goal. For an attacker, this information makes phishing the user significantly easier.
EthWalletSecurity interactively demonstrates how a phony notification for an incoming transaction would likely be enough for a user to unlock their MetaMask, and thus expose their wallet address, balance, and transaction history.
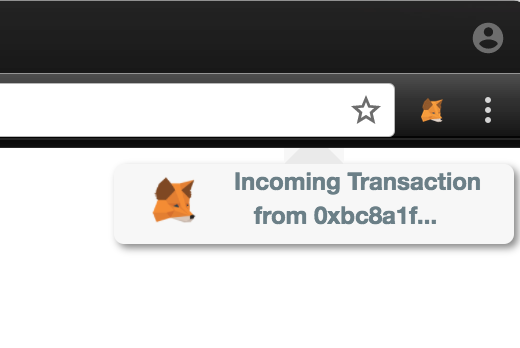
Approach #5: Phishing the User
The alternative to having the user open their real MetaMask is to create a fake MetaMask popout for the user to enter their password, seed phrase, or unencrypted private keys. Having a password is valuable, but an attacker would still need access to the user’s encrypted private keys. Having the user’s seed phrase or unencrypted private keys is game over for the user.

Approach #6: The Timing Attack
As mentioned in this blog post by co-founder John Backus, the malicious site can wait in the background until it detects you have unlocked MetaMask in a different tab. Presumably, you unlocked MetaMask in another tab because you were expecting to make a transaction on that site, whether a dApp or exchange. Since MetaMask does not tell you from which site a transaction originated, the malicious site (no longer the tab you’re currently viewing) can present you a transaction immediately upon detecting you unlocked your MetaMask, tricking you into thinking it came from the site you expected.
EthWalletSecurity provides users a chance to experience this timing attack firsthand. You can recreate this attack yourself by visiting the site with a locked MetaMask extension. Once on the site, open a different tab to a different site, and unlock your MetaMask there. Despite being in the background, EthWalletSecurity detects that you have unlocked your MetaMask in a different tab and presents you with a transaction immediately upon your unlocking!
Concluding Thoughts
Bloom is committed to making interacting with Ethereum dApps more secure, whether from a Chrome extension or from the command-line.
We encourage you to explore EthWalletSecurity and learn more about your wallet security. The site is highly interactive. Interacting with EthWalletSecurity from a locked MetaMask shows you different content and attack vectors than when you visit it from an unlocked wallet. We encourage users to learn about both sets of attack vectors, and to stay vigilant when issuing transactions.

